The following article comes from Chris Wake , the founder of Atypical, a venture fund. Chris spoke at last week’s Family Wealth Report Family Office Cybersecurity Forum. Chris explores the effect that AI, for example, has on the cybersecurity calculus.

Chris Wake
The same technologies that enabled generational wealth creation have become the greatest threat to preserving it. This paradox lies at the heart of modern cybersecurity challenges facing ultra-high net worth families and their offices.
The velocity-vulnerability connection
For generations, wealthy families understood a fundamental truth: speed creates opportunity. Faster capital movement, quicker decisions, and real-time market access each provided competitive advantages that built fortunes. But here's what wasn't anticipated – every system that increased velocity also increased visibility, and every efficiency created a new attack surface.
The evolution from physical ledgers to computers to smart phones to AI assistants has been a double-edged sword. Each technological leap forward that made family offices more efficient also made them more exposed. Virtually every family office that once operated in relative obscurity now has a digital footprint spanning continents.
From social engineering to social architecture
Traditional social engineering was a slow, methodical approach to infiltrating organizations. Today's threat landscape has evolved into something far more sophisticated: social architecture. Adversaries aren't using just one AI tool anymore – they're orchestrating entire ecosystems of artificial intelligence.
The speed differential is staggering. Modern AI systems can create a fake consulting firm in 60 seconds, complete with AI-generated headshots and LinkedIn profiles, then target family members or board members with direct outreach. Where social engineering was slow and labor-intensive, social architecture is incredibly fast and scalable.
The time factor: AI vs. human response
Consider this scenario: An AI-powered attack begins targeting your family office. Within the first minute, AI systems have initialized, scraped public data, and identified target profiles while your organization continues normal operations, completely unaware.
By 30 seconds in, fake personas are generated, and outreach content is created. At 45 seconds, a coordinated attack launches across multiple vectors – and only then do you receive your first security alert. Within 60 seconds, the breach is achieved with complete social architecture deployed, while your security team is just beginning to mobilize.
This isn't theoretical – this represents the current speed gap between AI-powered attacks and human response capabilities.
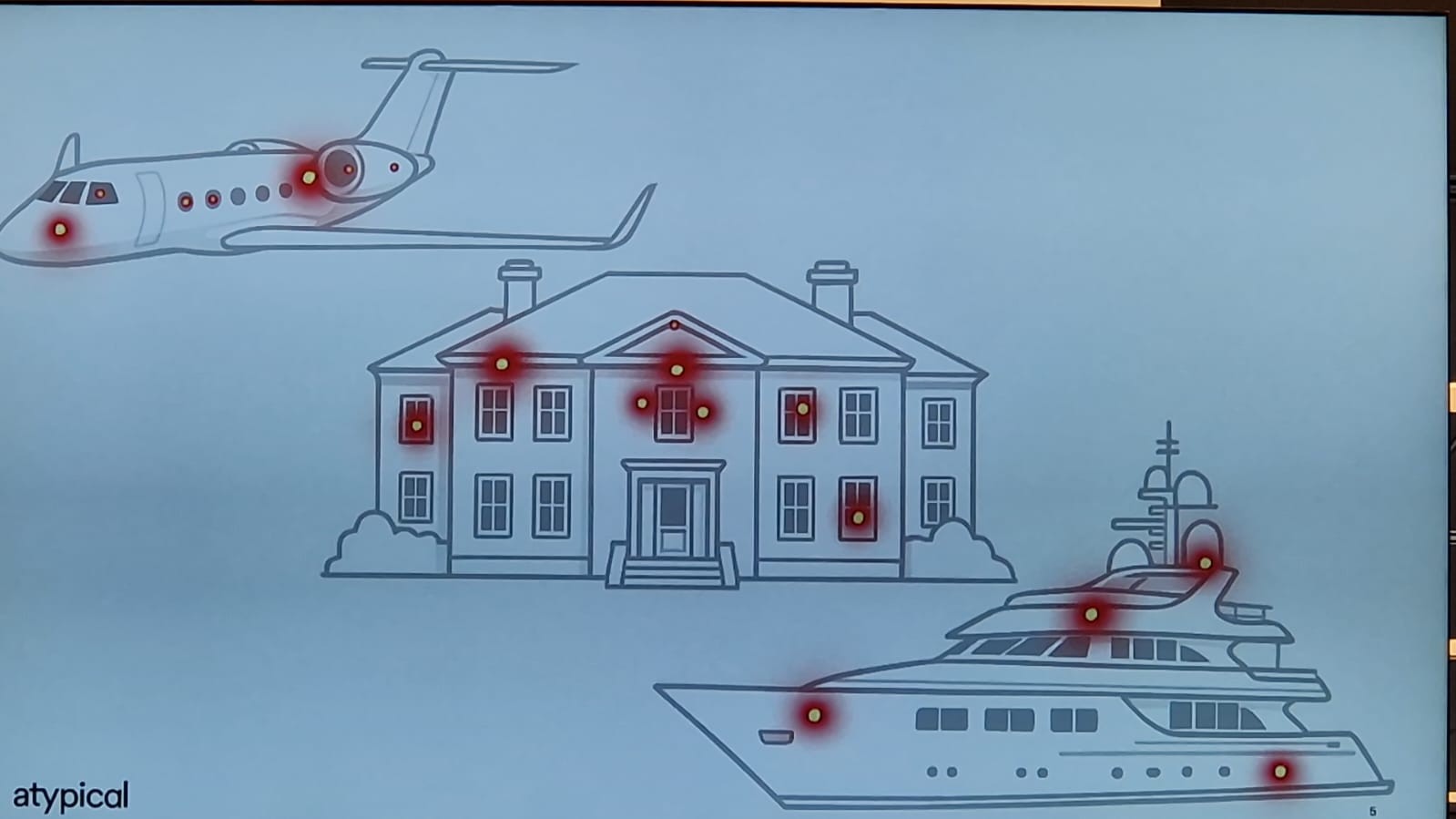
Threats
The invisible compromise
Perhaps even more concerning than social engineering attacks is how AI can exploit systems directly, without needing to trick humans at all. What appears as a secure digital ecosystem to IT teams – with all systems showing green status indicators – looks entirely different through an AI lens.
Where humans see individual, secure systems, AI identifies interconnected vulnerabilities and maps attack paths. It might start with weak guest access in collaboration tools, harvest credentials, access email systems, find cloud storage keys, and ultimately compromise investment platforms. The front door may be locked, but AI can identify dozens of windows that humans never knew existed.
Beyond higher walls: intelligent coordination
The traditional cybersecurity approach of building higher walls and stronger defenses is fundamentally mismatched with this new threat landscape. The future of family office security isn't about creating impenetrable fortresses – it's about intelligent coordination.
AI defense systems operate on an entirely different paradigm. While human security teams are still assembling to respond to an alert, AI defensive systems can detect threats, coordinate across dozens of different systems, block attacks globally, share intelligence with other defensive networks, and update security protocols – all in under a minute.
This represents a shift from reactive, human-dependent security to proactive, coordinated defense. Traditional security operates at human speed; AI defense operates at machine speed with human oversight.
The path forward: speed as an asset
The solution isn't to slow down operations for security – it's to speed up intelligently. The same velocity that created success can protect it when properly harnessed. Rather than building fortress walls around assets, family offices should focus on creating or purchasing intelligent networks that share threat intelligence instantly.
This approach provides coordination at machine speed while maintaining human oversight and decision-making authority. It's about moving from defensive thinking to intelligent offensive security – using AI to fight AI.
Trust vs fear decision
The fundamental question facing family office leadership isn't whether AI will reshape cybersecurity – it already has. The question is: who's holding the technological lever? As Archimedes said, "Give me a lever long enough, and I shall move the world." AI has become that lever in cybersecurity.
The challenge for family offices is determining whether they're moving at the speed of trust or still operating at the speed of fear. Those who embrace intelligent, AI-powered defensive systems will maintain their competitive advantages while protecting their assets. Those who rely solely on traditional security approaches will find themselves increasingly vulnerable to attacks that move faster than human response capabilities.
Conclusion
The technologies that built generational wealth don't have to become their undoing. By understanding the new threat landscape and embracing AI-powered defensive coordination, family offices can turn their greatest vulnerability – speed and interconnectedness – back into their greatest strength.
Speed built these fortunes. Speed, protected by artificial intelligence, will preserve them for generations to come.
About the author
Chris Wake is the founder of Atypical, an early-stage venture fund investing in plausible science fiction. He brings two decades of experience as an operator to his investing, including work on both hardware and software in the fields of aerospace, AI, and cybersecurity. Chris was a co-author on Commercial Space Systems Security Guidelines, and he has advised and invested in several foundational security and AI ventures. For instance, he has invested in AI infrastructure, supercomputing, AI semiconductors, xIOT security, continuous authentication, trust infrastructure for payments, and search rebuilt for AI. Two noteworthy investments for the Summit audience include: BKLN and Norm, each of which serve major asset managers.
